We've probably all encountered one by now – a phishing email. Whether it’s a rush to settle an unexpected invoice or a faux CEO urging us to click on a questionable link, phishing attempts vary in complexity. And they’re becoming more challenging to spot.
Phishing remains one of the most pervasive threats in the digital landscape and is especially common in email. 57 per cent of organisations are facing phishing attacks weekly or daily. But there are steps you can take to improve your standing.
We’ve talked to the expert — Kyle Tackley, Senior Principal at DataGuard’s Information Security and Privacy Practice — to draw insights into identifying and preventing email phishing attacks to secure your team.
In this article:
- What is phishing?
- 6 ways to recognise email phishing attempts
- How to prevent your organisation from phishing attacks
- What should you do if your organisation has fallen victim to phishing?
- Phishing is here to stay - be ready
What is phishing?
At their core, phishing attacks are social engineering techniques that exploit human psychology to deceive people into taking actions that harm their security.
These attacks often involve emails, text messages, or phone calls that appear to be from legitimate sources, such as banks, credit card companies, or online retailers. The goal is to trick recipients into clicking on malicious links, opening infected attachments, or divulging personal information.
6 ways to recognise email phishing attempts
It’s easy to get caught off guard. Have you ever been at the airport, juggling duty-free bags, coffee, and your sanity while checking emails?
“That's the sweet spot for phishing attacks because we can easily click on something we shouldn’t when distracted”, says Kyle Tackley. With half our daily inbox intake being spam, it can be tricky to see what’s genuine and what’s not.
1. Make sure you know who sent it
Cybercriminals often employ subtle variations in email domains to mimic legitimate entities. So, step one in verifying the credibility of an email is checking the sender. For instance, a fraudulent email might feature "paypall.com" instead of the authentic "paypal.com” or “accountprotectionmicrosoft.com” instead of “microsoft.com”.
Scammers may even spoof the email by forging the email header to make it look like it came from a trusted entity. Then, the actual sender can only be revealed through closer header inspection.
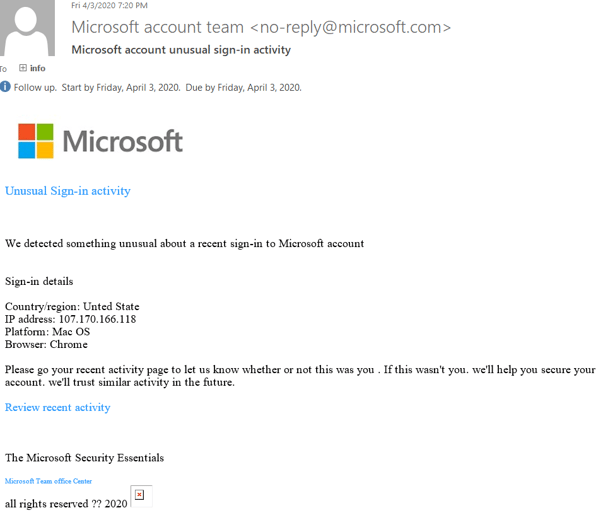
Source: Genesis
A phishing email may also impersonate a high-ranking executive, often the CEO, and, for example, request an urgent wire transfer. The email may seem authentic, complete with the executive's signature and brand logo. However, a careful examination reveals subtle differences in the email address or communication style.
Watch our on-demand webinar: New cyber threats: your voice is my password
2. Spot awkward phrasing or grammar mishaps
With the sender identified, the next step is investigating the email content. Watch for awkward phrasing, unusual requests, generic or weirdly official greetings (Dear Sir/Madam), and grammar mishaps. These classic red flags have long been our allies in detecting phishing attempts. However, the game is changing.
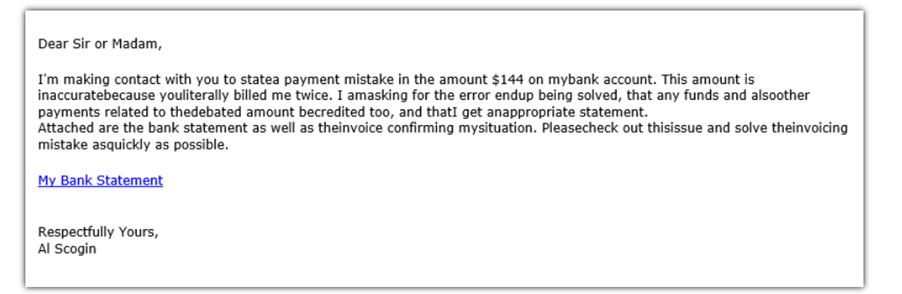
Source: Hashed Out
Scammers are getting an upgrade with AI, and now, even poorly written emails can sound eerily human. Sure, they may still slip up, but the margin for error is shrinking. So, while keeping an eye out for the classic tell-tale signs, also trust your instincts. If something feels off, it probably is.
3. Check for unwarranted urgency
Cybercriminals love to play the urgency card, preying on our instinct to react quickly in a crisis. For example, users may receive an email about a critical software update to address security vulnerabilities. It may include a link that, when clicked, directs the recipient to a fake website where their login credentials are harvested.
Legitimate entities seldom employ coercive measures in their communication. So if an email screams, "Payment request urgent action needed” or "Your account has been compromised - update your details now", it’s most likely a phishing attempt.
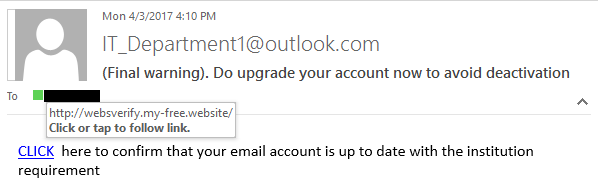
Source: MSVU
4. Are they asking for sensitive information?
Most companies understand the importance of secure communication channels and know the risks of soliciting sensitive information via email.
Therefore, any unsolicited email requesting personal details or banking information should immediately raise suspicion. Scammers often use this tactic to exploit individuals who may not be fully aware of cybersecurity best practices.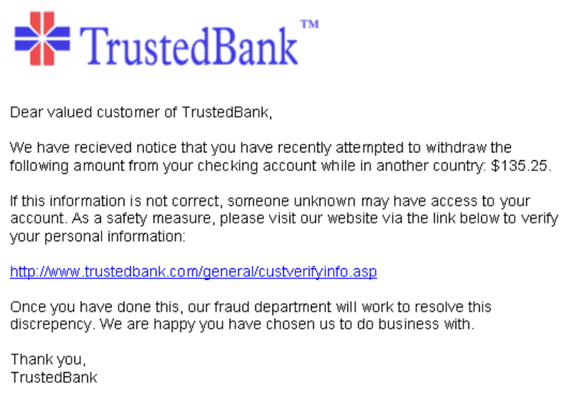
Source: The State Bank Group
5. The hottest trend – compromised QR codes
QR codes, commonly used for quick access to websites or information, have become a new vector for email phishing attempts. Here, attackers manipulate legitimate QR codes or create counterfeit ones that, when scanned, lead unsuspecting individuals to malicious websites.
These sites are often meticulously designed to mirror trusted platforms, making it difficult for users to discern the deception. Tell your team to double-check QR codes and not scan anything suspicious. Keep them in the loop about these new tactics so they stay sharp.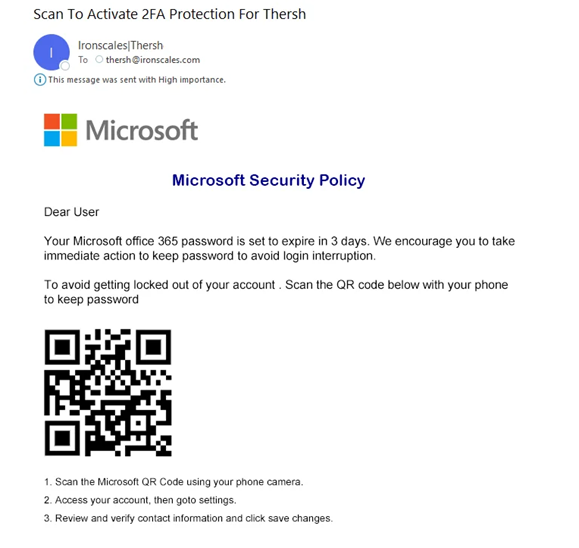
Source: Reddit
6. Beware of suspicious links, forms or attachments
A common tactic employed by cybercriminals is to embed seemingly harmless links in emails, luring unsuspecting recipients into clicking. These links can initiate the download of malicious software, compromising the security of the user's device and potentially extending the threat to the entire network.
Similarly, attachments in phishing emails may contain malicious elements capable of exploiting vulnerabilities in the recipient's system upon opening.
As Kyle Tackley states: “Every organisation tends to have “serial clickers” – users who are more likely to click on something without thinking. This is where employee awareness and education come in.”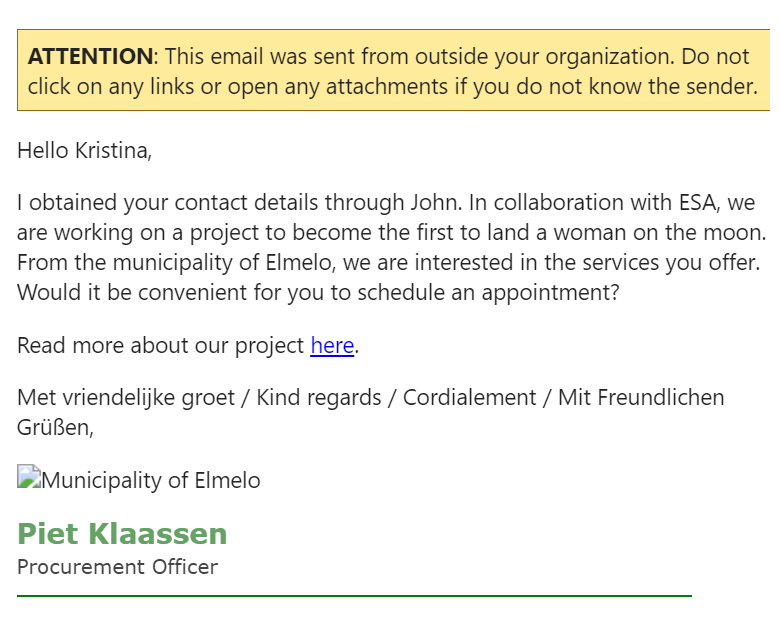
Source: DataGuard
The example above shows a screenshot of a phishing simulation email recently sent to DataGuard‘s employees. Using the insights we’ve already covered, it is pretty apparent this is a phishing attempt (if a fake one). The moon mission is the first dead giveaway; the phrasing is formal and awkward, and if you check the person and their company online – they do not exist. The Elmelo municipality is also misspelt; the correct name is Almelo.
But in the unlikely case that anyone clicks on “here”, they are taken to an employee awareness page to get more information on how to stay informed and protected from phishing attacks, which brings us to the next section.
How to prevent your organisation from phishing attacks
More than 80 per cent of reported security incidents are phishing attacks. The digital landscape is full of hidden traps, and the last thing you want is to be the unwitting star of a cyber-horror story.
Educate your crew
Conduct regular awareness and education programs, emphasising the importance of recognising and reporting phishing emails. Teach your employees to spot potential scams and report threats.
Equip your team with the knowledge to recognise the signs, question every link, and navigate the web safely. Creating a culture of scepticism and caution can empower employees to question the legitimacy of incoming emails and attachments, strengthening your organisation's defences against phishing attacks.
Set up reliable systems
The key here is to have a reliable tech stack and information security measures in place. Utilise robust email gateway solutions to filter out malicious content before it gets to users. Have backup solutions, especially for databases, to ensure data recovery in case of compromise.
Test your defences - simulate phishing attempts
Simulating phishing emails across the organisation (provided only a few key individuals know about the simulation) helps identify vulnerabilities.
"Clicking on a simulated phishing email could prompt immediate awareness training, educating employees on what to watch out for in real scenarios to minimise risks,” says Kyle Tackley.
What should you do if your organisation has fallen victim to phishing?
According to Kyle Tackley, ISO 27100 guidelines are a good place to start if a phishing attack hits your organisation. Solid incident response processes and a straightforward data incident reporting procedure are key.
“Affected employees need to know what to do, even if unsure if they've dealt with a sketchy email,” he says.
When in doubt, users should log a ticket or reach out to kickstart the communication chain. It's not solely up to employees to decide if a security incident occurred, but they should be savvy enough to know when to report it.
Phishing is here to stay - be ready
As the bad players get craftier, we're looking at a future where scammers team up with generative AI and voice cloning. That means a convincing phishing email may be reinforced with a convincing voice message, laying the ground for a successful scam.
Organisations must stay vigilant, regularly train their workforce, and adopt advanced technologies to safeguard against phishing attacks. Nobody is immune, but with the proper precautions, you can significantly reduce the risks associated with phishing attacks.
Reach out to DataGuard if you need more help and guidance on preventing your organisation from phishing.










