Don’t miss these topics:
Related Resources
Bringing complete peace of mind
to over customers




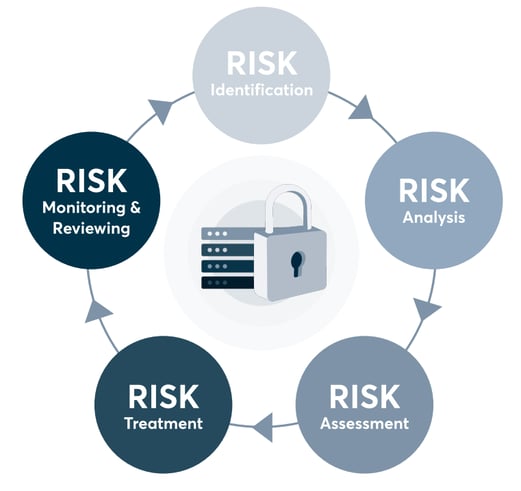
This guide looks at the five key steps you need to consider to start on your risk management journey



To start identifying risks to your business, you need to assess your information assets, internal and external threats, and any vulnerabilities in your Information Security Management System (ISMS). But before starting on your assessment, it is important to establish your risk assessment framework.
For your risk assessments to be auditable, objective, and transparent, your process must be consistent, valid and comparable every time you do one. A risk assessment framework is a set of guidelines which ensures just that.
These guidelines must address:
When assessing risks for an asset-based risk assessment, consider your organisation's different asset types, including information and data, hardware and software, physical locations and storage, systems and services, people, organisations, and intangibles. An asset database will further help you conduct the assessment, where you can easily classify and assign responsibility to each asset.
Once the risks are identified, they should be allocated to risk owners, who are responsible for the risk management process.
Assets may have several threats which can be exploited via multiple vulnerabilities in your system. It is essential to analyse and assess the likelihood of each combination of threat and vulnerability and their impact during the risk assessment. The outcomes of the analysis should also be reflected in the Risk Assessment and Treatment Table.
Ranking risks based on their consequences and likelihood would help your organisation deploy its resources effectively and reduce redundancy. Through this, you can determine which hazards need to be prioritised and controlled immediately to prevent a possible security breach.
| Overall Risk = Likelihood x Consequences |
To start treating your risks, creating a Statement of Applicability (SoA) is essential. An SoA demonstrates your security posture by showing the controls you’ve chosen and the justification for their use, the controls you’ve implemented and how you’ve implemented them, and your justification for omitting any ISO 27001 Annex A controls.
Next, it is time to formulate a Risk Treatment Plan (RTP). The RTP is an action plan specifying the controls to be implemented, the responsible parties, the planned deadlines and the required resources. Risks are usually treated by transferring the risk to a third party, avoiding risks by divesting from the activity, reducing risk levels by employing mitigation strategies or accepting the risk to to control and tolerate it internally.
It is highly recommended to repeat risk assessments annually and monitor risks continuously. Involving your employees in the risk management process, management reviews and internal audits can help you stay on top of your changing ISMS and risks.

Understanding the steps involved in risk management can help you streamline your process and improve your cyber resilience. At first glance, implementing the many steps of risk management can seem daunting. But with the right tools and expert advice, you can ensure your organisation’s risk management process is successful.
Risk management is a crucial step in getting ISO 27001 certified. If you feel overwhelmed by the complexity of implementing effective risk management, talk to one of our experts. We speak your language and can help you with every step to make your risk assessment a success.
Bringing complete peace of mind
to over customers




Find out how our Privacy, InfoSec and Compliance solutions can help you boost trust, reduce risks and drive revenue.
100% success in ISO 27001 audits to date
TISAX® is a registered trademark of the ENX Association. DataGuard is not affiliated with the ENX Association. We provide consultation and support for the assessment on TISAX® only. The ENX Association does not take any responsibility for any content shown on DataGuard's website.